Docker Compose for NextCloud with Traefik 2 (SSL)
Intro
I set up Traefik 2 on a VServer at Netcup mainly to use Nextcloud. Since I am neither Docker nor Traefik or NextCloud expert it took some time to set up everything as most of the docker-compose.yml files I found weren't working. So here is my short story about setting up NextCloud.
Complete docker-compose.yml
version: '3.7'
services:
db:
image: mariadb:latest
container_name: nextcloud_db
volumes:
- nextcloud-db:/var/lib/mysql
networks:
- default
restart: always
environment:
TZ: UTC
MYSQL_ROOT_PASSWORD: SUPER_SECRET
MYSQL_DATABASE: db
MYSQL_USER: admin
MYSQL_PASSWORD: SUPER_SUPER_SECRET
redis:
image: redis:latest
container_name: nextcloud_redis
restart: always
networks:
- default
volumes:
- nextcloud-redis:/var/lib/redis
nextcloud:
depends_on:
- redis
- db
image: nextcloud:stable
container_name: nextcloud
volumes:
- nextcloud-data:/var/www/html
networks:
- web
- default
restart: always
labels:
- traefik.http.routers.nextcloud.middlewares=nextcloud,nextcloud_redirect
- traefik.http.routers.nextcloud.tls=true
- traefik.http.routers.nextcloud.tls.certresolver=lets-encrypt
- traefik.http.routers.nextcloud.rule=Host(`cloud.YOUR-DOMAIN.com`)
- traefik.http.middlewares.nextcloud.headers.customFrameOptionsValue=ALLOW-FROM https://YOUR-DOMAIN.com
- traefik.http.middlewares.nextcloud.headers.contentSecurityPolicy=frame-ancestors 'self' YOUR-DOMAIN.com *.YOUR-DOMAIN.com
- traefik.http.middlewares.nextcloud.headers.stsSeconds=155520011
- traefik.http.middlewares.nextcloud.headers.stsIncludeSubdomains=true
- traefik.http.middlewares.nextcloud.headers.stsPreload=true
- traefik.http.middlewares.nextcloud.headers.customresponseheaders.X-Frame-Options=SAMEORIGIN
- traefik.http.middlewares.nextcloud_redirect.redirectregex.permanent=true
- traefik.http.middlewares.nextcloud_redirect.redirectregex.regex=https://(.*)/.well-known/(card|cal)dav
- traefik.http.middlewares.nextcloud_redirect.redirectregex.replacement=https://$${1}/remote.php/dav/
environment:
REDIS_HOST: redis
MYSQL_HOST: db:3306
MYSQL_DATABASE: db
MYSQL_USER: admin
MYSQL_PASSWORD: SUPER_SUPER_SECRET
TRUSTED_PROXIES: 172.18.0.1
networks:
web:
external: true
volumes:
nextcloud-data:
nextcloud-db:
nextcloud-redis:
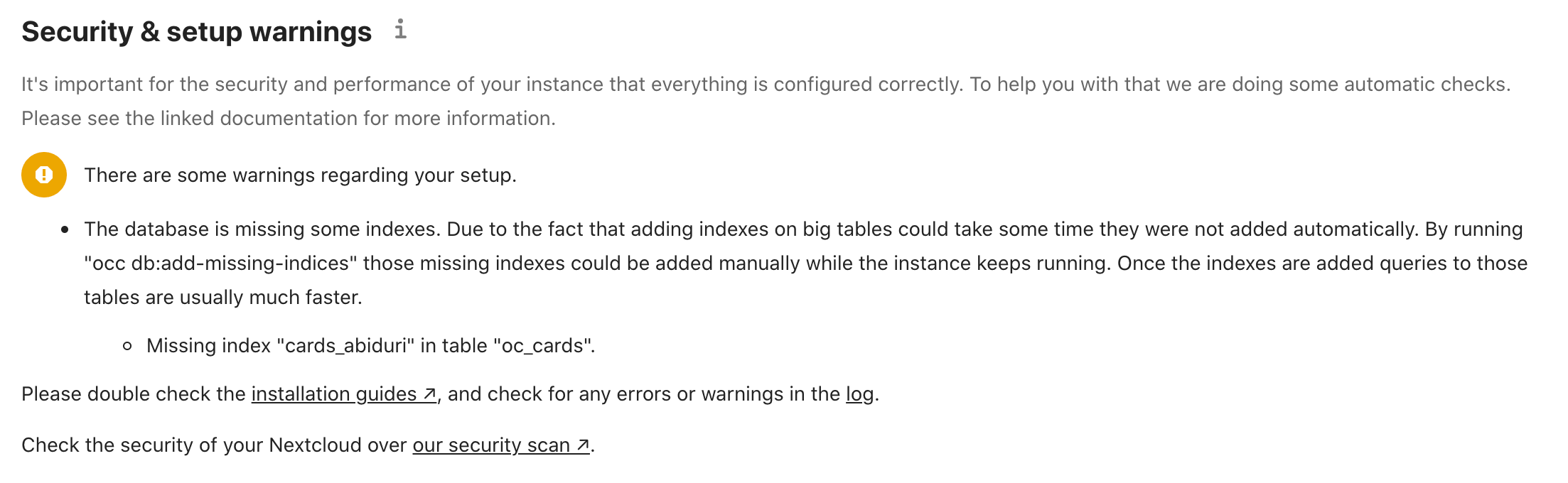
Test your set up and security
After you fired up your Nextcloud you should check if everything is working as expected. NextCloud offers two ways to help you with that:
- Settings > Administration > Overview
- Security check
Usage of calDav and cardDav
It's quite easy if you use the docker-compose.yml above. You need your domain, your user and as it is recommended an app password (Settings > Security > "Create new app password"). With these credentials you can go to every client which supports calDav/cardDav. In the screenshot below you can see a calDav set up in the iOS settings.
- Server: cloud.YOUR-DOMAIN.com
- User: user
- Password: app password
All the links I found and read
I spent some hours in setting up all of these, here is a list with all the links I used. The DigitalOcean Tutorials are just awesome and as far as I can tell are always up to date. I only would start Traefik as a docker-compose.yml to be consistent.
- Server: Initial Server Setup with Ubuntu 20.04, How to Set Up SSH Keys on Ubuntu 20.04
- Traefik: How To Use Traefik v2 as a Reverse Proxy for Docker Containers on Ubuntu 20.04, Traefik 2.x configuration
- NextCloud Docker (with Traefik): WhiteBahamut/nextcloud, nextcloud/docker, Running Nextcloud With Docker and Traefik 2, Notes on traefik v2, Nextcloud, etc., ismailyenigul/nextcloud-pgsql-redis-traefikv2-docker-compose.yml, CVJoint/traefik2, pamendoz/personalDockerCompose, Self Hosted Nextcloud Using Docker, Cannot make https work properly with Docker + Traefik v.2
- NextCloud problems: Nextcloud really slow after installation, [Help] Add a carddav account to macOS